OpenID Connect (OIDC) and SCIM are available on Pro & Enterprise plan only.
OpenID Connect (OIDC)
This integration allows your organization to utilize its existing identity provider (IdP) services to manage user access to All Quiet.Step-by-Step-Guide
Create an Organization
To use OIDC, you first need to create an Organization in All Quiet. If you also want to use SCIM to provision your users, please note that the user (“root user”) who creates the Organization cannot be provisioned through SCIM. We recommend to create the Organization with a “root user” that is not bound to a specific employee, like devops@yourcompany.com.
Contact All Quiet Support
Begin by reaching out to our support team at support@allquiet.app. Provide details about your organization and the identity provider you are using. Our team will assist you with the initial setup process and provide necessary guidance.
Setting up in Your IdP
In your identity provider’s management console, you will need to register All Quiet as a new application.For the integration, you will need to provide the Client ID, Client Secret, and the Authority URL from your IdP. The Authority URL is usually the client-specific domain derived from the discovery document URL. These details are essential for establishing a secure and reliable connection between your IdP and All Quiet.Also, you’ll need to configure the Redirect URI in your IdP:
https://allquiet.app/signin-oidc(US Hosted) orhttps://allquiet.eu/signin-oidc(EU Hosted).
https://allquiet.app/login(US Hosted) orhttps://allquiet.eu/login(EU Hosted).
OIDC with Microsoft Entra ID
In your OIDC tenant’sAPI Permissions settings, add email, offline_access, openid and profile permissions.
Mark all these permissions as type Delegated and without requiring Admin consent.Also, in the Token Configuration, add email claims.OIDC with Jumpcloud
In your OIDC tenant’sOIDC Single Sign-On Configuration- Select “Client Secret POST” as
Client Authentication Type - Select Standard Scopes “Email” and “Profile”. No need to further adjust the mapping of single attributes.
Verification and Testing
Once the setup is completed, our team at All Quiet will perform a series of tests to verify the integration. This ensures that authentication requests are properly handled and user identities are correctly established through your IdP.
While All Quiet aims to make the integration process as straightforward as possible, we do not offer a self-service option for this setup. Our support team is dedicated to assisting you through each step of the process and ensuring the integration meets your organization’s specific needs.
Conclusion
Integrating your organization’s SSO using OpenID Connect with All Quiet enhances your platform’s security and user experience. With this setup, you ensure a consistent and secure access management system, aligned with your organizational policies and requirements.SCIM 2.0
Step-by-Step-Guide
For this process, you need access to the API Keys and SSO tabs of you organization, only accessible to users with Organization Owner role.
Create an Organization
To use SCIM, you first need to create an Organization in All Quiet. Please note: The user who creates the Organization cannot be provisioned via SCIM. Therefore, we recommend to create the Organization with a “root user” that is not bound to a specific employee, e.g. devops@yourcompany.com. This way, you ensure all “real” on-call users and employee accounts can be provisioned. If you already set up the Org with your personal account, you can change your account’s email address via the Web app on /app/account to a root user email and later provision your personal email and account via SCIM.
Contact All Quiet Support
Begin by reaching out to our support team at support@allquiet.app. Provide details about your All Quiet Organization and the SCIM provider you are using. Our team will assist you with the initial setup process and provide necessary guidance.
Have you already created users manually and now wish to convert them to SCIM-provisioned users? Let us know during this step.
Retrieve Base URL & API Key
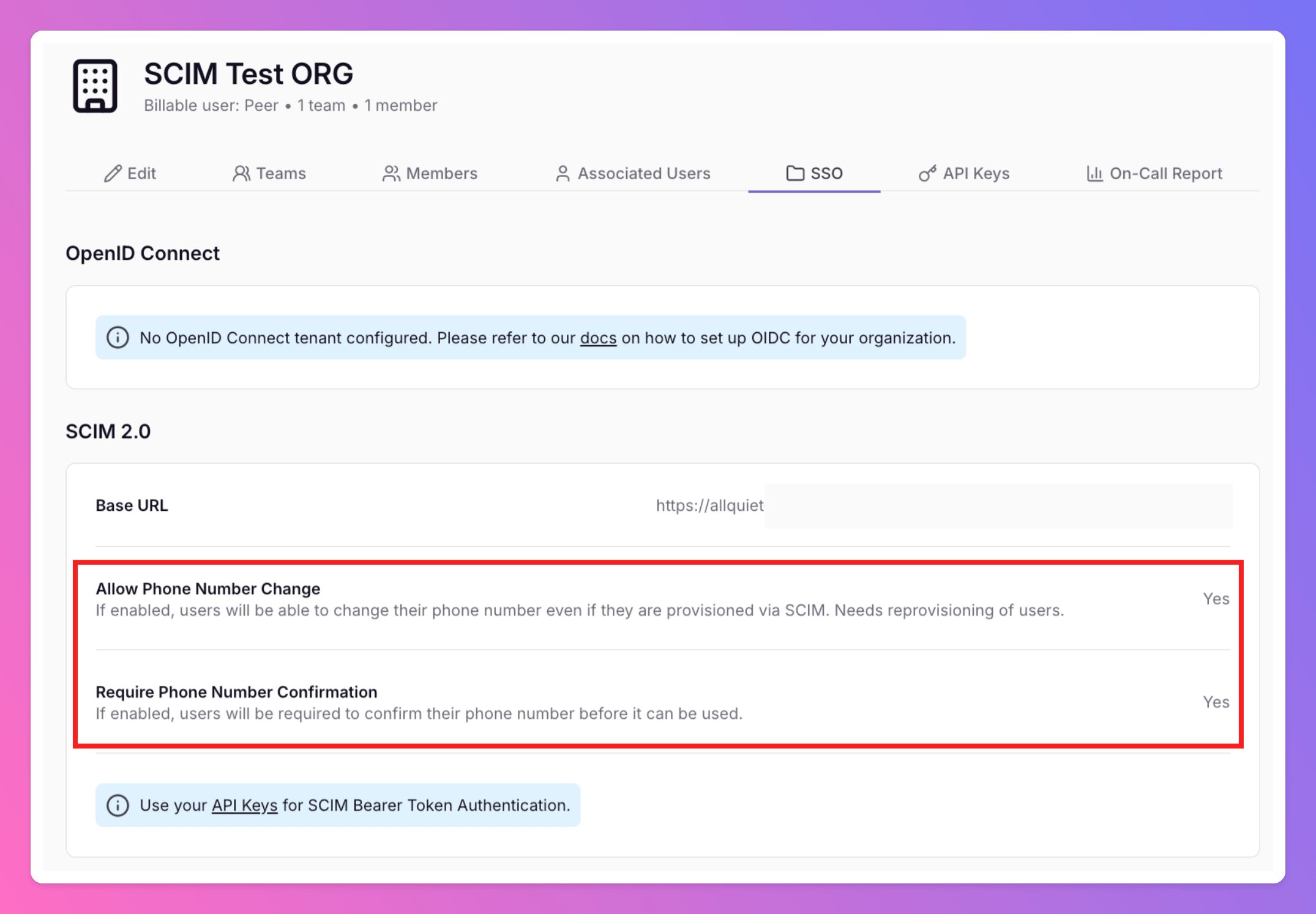
In your SCIM provider’s console, you will need to register All Quiet as a new SSO application.For the integration, you will need to provide the Base URL and API Key of your All Quiet Organization.After getting in touch with our team, we will create your Organization’s Base URL. It will be visible under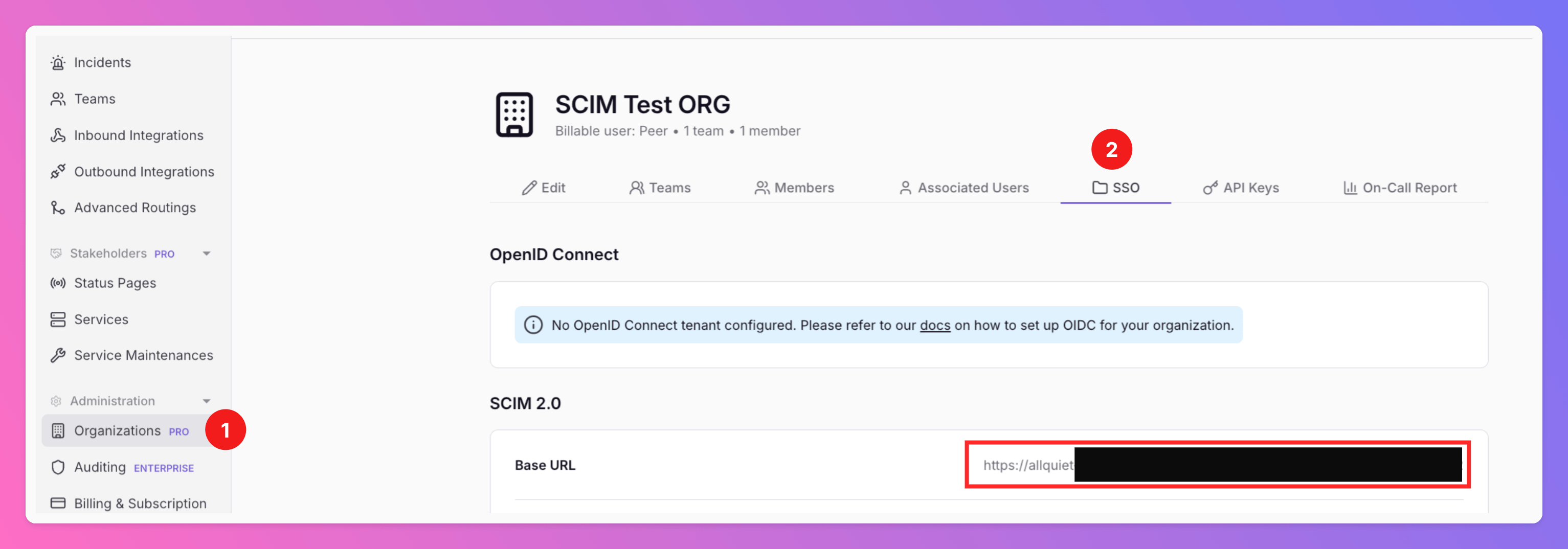
Organizations.- Select your Organization and the tab
SSO.

Organizations.- Select your Organization and the tab
API Keys. - Retrieve your
API Key. - Alternatively, click
+ Create API Keyif you haven’t created one yet.

Verification and Testing
Once the setup is completed, you will find the users provisioned via SCIM under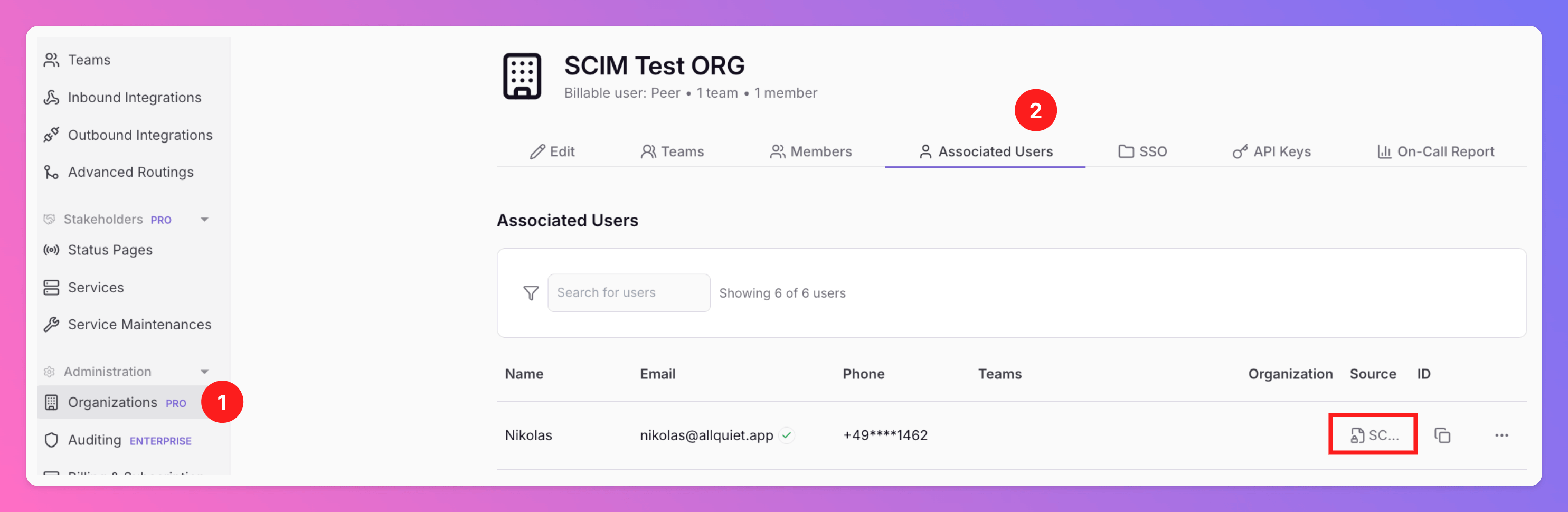
- Organizations
- Tab
Associated Users. TheSourcecolumn will show which users got provisioned via SCIM.

SCIM Team & Organization Role Provisioning
You can use the User Groups from your SCIM provider for Team & Organization Management in All Quiet. This is a convenient and much leaner alternative to manual team invites for larger organizations.Go to 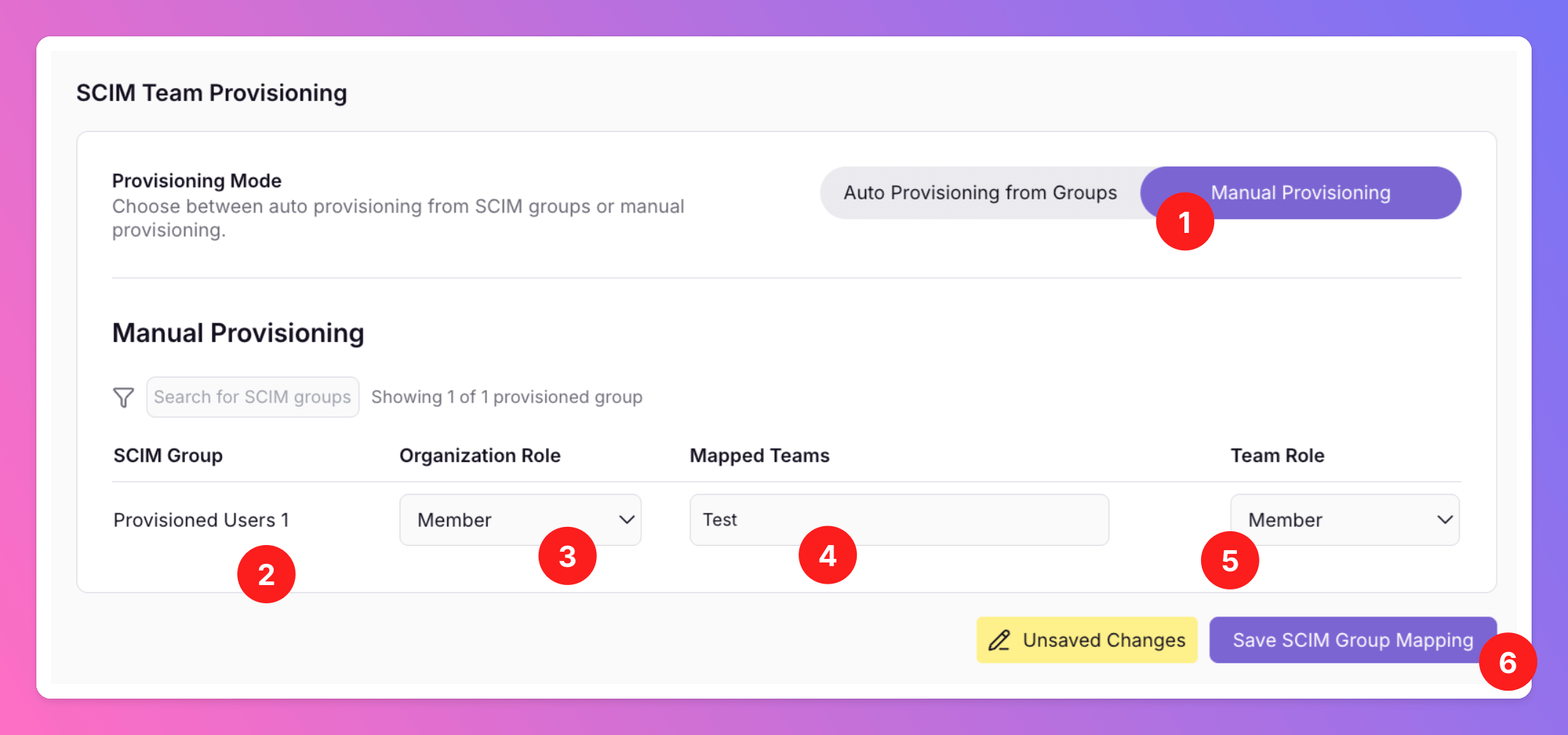
Organizations > SSO.Manual Provisioning Mode-
First, you need to select your
Provisioning Mode. We recommendManual Provisioningif you want to be flexible and want to be able to switch SCIM User Groups between All Quiet Teams. - Find your SCIM User Groups below.
- Optionally, you can assign Organization Member, Organization Administrator or Organization Owner roles to the provisioned users.
- Map your SCIM User Groups to All Quiet Teams. For Manual Provisioning Mode, there have to be existing teams for you to be able to map them.
- Choose whether provisioned users should be assigned Member or Administrator roles within the teams. You can update these roles via the Teams section at any time for each User. Learn more about team roles here.
- Save your settings. You will find the Users from your SCIM User Groups in your All Quiet Teams.

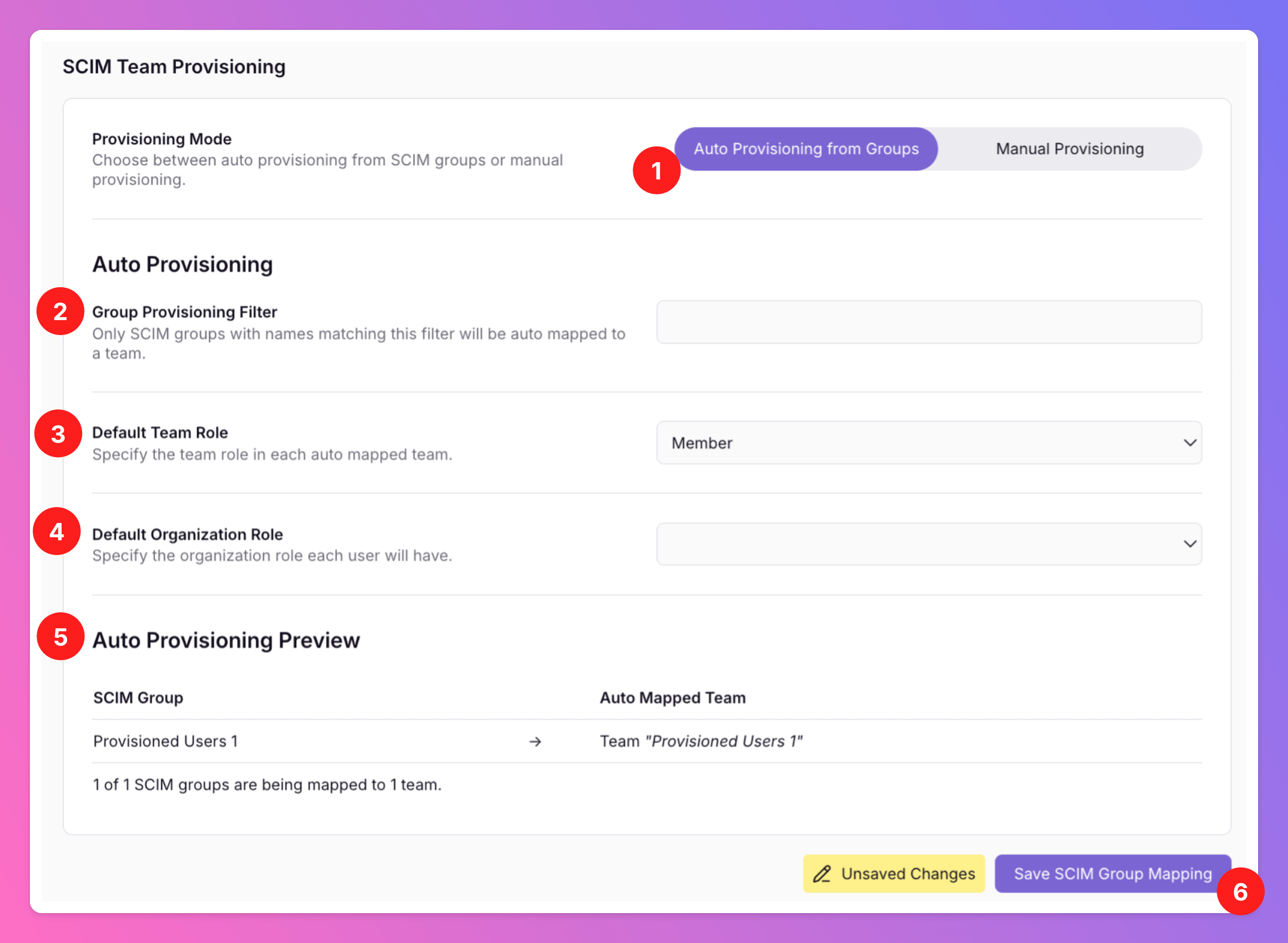
- In this case, we’ve selected Auto Provisioning from Groups as provisioning mode. For this mode you don’t have to create All Quiet teams in advance. However, it’s also much stiffer.
- Auto Provisioning options include a Group Provisioning Filter: You can use this field if you only want certain SCIM User Groups to be auto provisioned to All Quiet Teams.
- Default Team Role: Choose whether provisioned users should be assigned Member or Administrator roles within the Teams.
- Default Organization Role: You can additionally assign Member,Administrator or Owner roles within the Organization.
- A preview showing which SCIM User Groups will create which All Quiet Teams.
- Again, safe to create the teams and roles through auto provisioning mode.

Provisioned Users Cannot Be Edited via Web App.
To ensure that the resources managed via your SCIM provider stay in sync with your setup, we lock provisioned resources within the Web App. This means these resources cannot be edited or deleted directly through the Web App’s interface. Provisioned resources are marked with an icon, and hovering over it will display a message explaining why the resource is locked and cannot be modified via the Web App.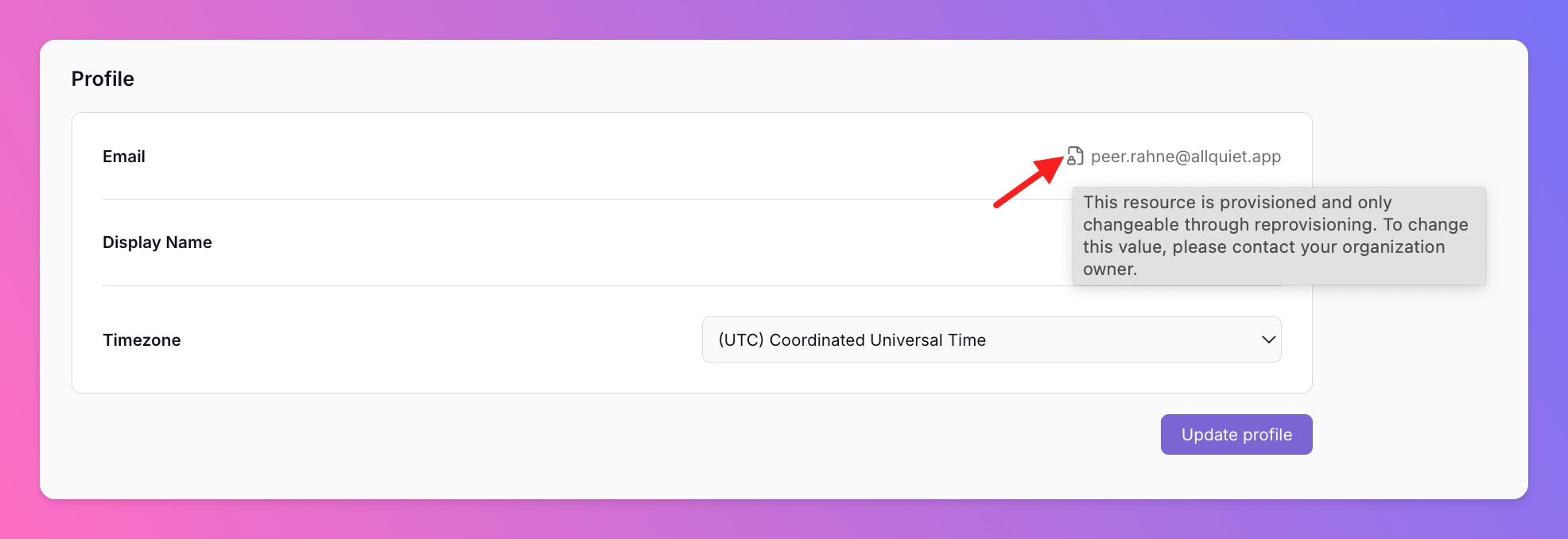
SSO page of your organization. If you want to change your settings, please contact support@allquiet.app.